
A new report from security researchers suggests a new trojan preying on Android users. It is first detected by ESET in November 2018, the malware combines the capabilities of a remotely controlled banking Trojan with a novel misuse of Android Accessibility services, to target users of the official PayPal app.
Once it is launched, the malicious app terminates without offering any functionality and hides its icon. The malware’s first function is stealing money from its victims; PayPal account holders. However, it requires the activation of a malicious Accessibility service. This request is presented to the user as being from the innocuous-sounding “Enable statistics” service.
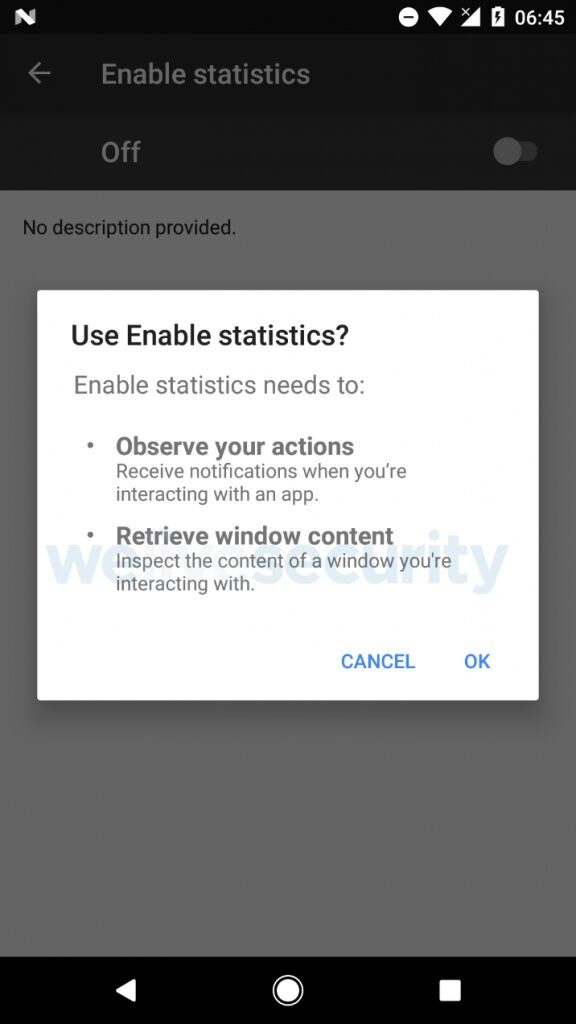
If the official PayPal app is installed on the compromised device, the malware displays a notification alert prompting the user to launch it. Once the user opens the PayPal app and logs in, the malicious accessibility service becomes active and mimics the user’s clicks to send money to the attacker’s PayPal address. The whole process takes about 5 seconds, and for an unsuspecting user, there is no feasible way to intervene in time.
Since the malware does not rely on stealing PayPal login credentials, it instead waits for users to log into the official PayPal app themselves, it also bypasses PayPal’s two-factor authentication (2FA). The attackers fail only if the user has insufficient PayPal balance and no payment card connected to the account. The malicious Accessibility service is activated every time the PayPal app is launched, meaning the attack could take place multiple times.
The malware’s second function leverages on phishing screens covertly displayed over targeted, legitimate apps. By default, the malware downloads HTML-based overlay screens for five apps Google Play, WhatsApp, Skype, Viber, and Gmail but this initial list can be dynamically updated at any moment. Unlike overlays used by most Android banking Trojans, these are displayed in lock foreground screen.
This prevents the victims from removing the overlay by tapping the back button or the home button. The malware’s code contains strings claiming the victim’s phone has been locked and can be unlocked by sending an email to a specified address. Additionally, the malware can also intercept and send SMS messages; delete all SMS messages; change the default SMS app, obtain the contact list, make and forward calls, obtain the list of installed apps, install the app, run installed app, start socket communication.
Interestingly, these Trojans also use Accessibility to thwart uninstallation attempts by repeatedly clicking the “Back” button whenever a targeted antivirus app or app manager is launched, or when strings suggesting uninstallation are detected in the foreground.
