Researchers from the cyber security firm Palo Alto Networks has discovered a new malware that can affect even non-jailbroken devices. The malware manages to install itself without any enterprise certificate unlike other malwares.
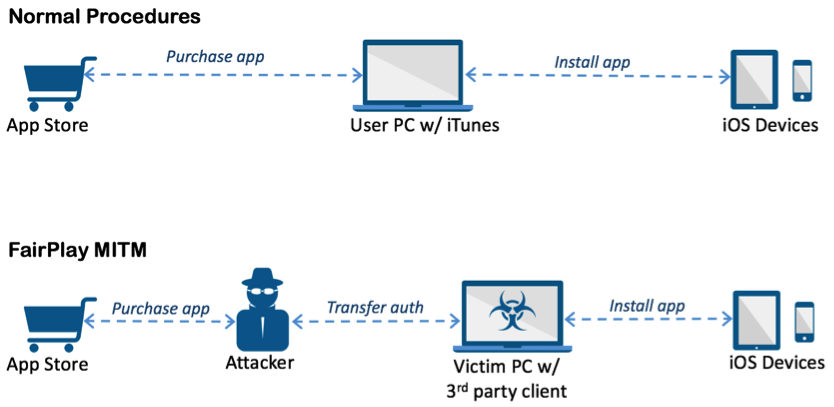
For those unaware, a jailbroken device refers to an iPhone or iPad that has been modified without Apple approval to install software and apps that are not officially available on the Apple App Store. According to the research firm, AceDeceiver installs itself by exploiting design flaws in Apple’s DRM mechanism. Even though Apple has removed AceDeceiver from App Store, it may still spread due to a novel attack vector. The iOS malware is said to abuse certain design flaws in Apple’s DRM protection mechanism that is dubbed as FairPlay, to install malicious apps on iOS devices regardless of whether they are jailbroken. The research firm says this is the first time it has seen FairPlay Man-In-The-Middle (MITM)” attack being used to spread malware.
Claud Xiao, a security researcher from Palo Alto Networks, wrote in a blog post,
In the FairPlay MITM attack, attackers purchase an app from App Store then intercept and save the authorization code. They then developed PC software that simulates the iTunes client behaviors, and tricks iOS devices to believe the app was purchased by victim. Therefore, the user can install apps they never actually paid for, and the creator of the software can install potentially malicious apps without the user’s knowledge.
Attackers used a popular tool called Aisi Helper Windows, which runs on the Microsoft OS. When users downloaded Aisi Helper, the system would automatically try to download the malware from the Apple App Store and silently install it on attached iOS devices. Three different iOS apps in the AceDeceiver family were uploaded to the official App Store between July 2015 and February 2016, and all of them claimed to be wallpaper apps. Apple has removed these three apps from the App Store.
However, the attack is still viable because the FairPlay MITM attack only requires these apps to have been available in the App Store once. The attack does not require current App Store availability to spread those apps, as long as an attacker gets hold of a copy of authorization from Apple. Currently, the AceDeceiver malware has only been spotted in China, but Palo Alto Networks warns that with small configuration tweaks it could affect other iPhone users globally.
In September last year, Apple’s App Store was hit by a major malware attack that had affected a number of apps while in October the YiSpecter malware was infecting non-jailbroken Apple devices using enterprise certificates and private APIs.
